Security is an essential component of any organization. It’s the reason we lock our doors at night. This is true of our homes as well as our businesses. As technology progresses, new threats to our security emerge, and new steps to address them.
When it comes to your cyber security, the danger is everywhere. This is especially true if you happen to be responsible for a cloud-based server filled to the brim with sensitive information. Fortunately, the cloud has a lock in the form of an SBC.
What is an SBC?
SBC stands for Session Border Controller. A session is any time when two parties communicate with one another like a call. A border is any separation between different parts of a network. A controller is what influences the data of the sessions as they move across the borders.
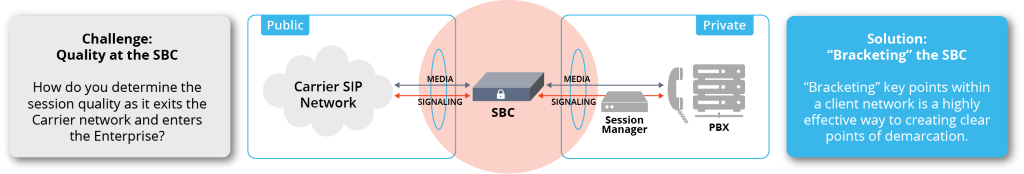
The key function of an SBC is to provide security for voice over internet protocol (VoIP). It monitors the session to ensure only authorized callers are allowed access as it moves along the borders. It encrypts signals and wards off malware and DDoS attacks. Calls are safeguarded with a functioning SBC.
Session Border Controller vs. Traditional Firewalls
SBCs are a lot like traditional firewalls in terms of network security. They manage bandwidth, vet communications, and keep out malicious abusers. The difference lies in their effectiveness in monitoring individual sessions and voice packets.
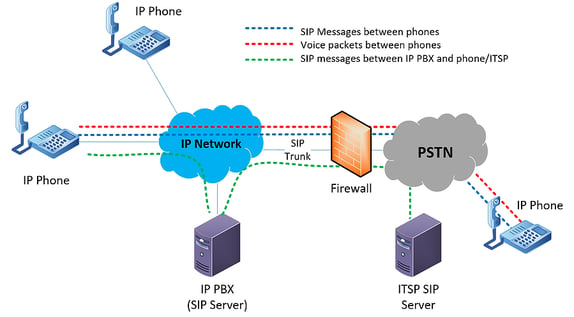
Each call your organization makes contains multiple sessions. A traditional firewall views each session individually, and may mistake one for a threat. It then denies that session access to the network, which may result in one way voice, no way voice, or disconnection.
Some traditional firewall users create firewall pinholes to get around this issue. A pinhole refers to a port that isn't protected by the firewall to allow sessions access to the network. The problem is a pinhole can be accessed by anyone outside your organization which is a serious breech in your security.
Installing an SBC allows you to monitor traffic more closely. You can grant access to voice traffic while ensuring malware and toll fraud stay out.
Service and Savings
An SBC will keep your sessions secure, eliminate interference, and ultimately improve the quality of your calls. They're also incredibly cost-effective. Using an SBC for SIP trunking services reduce traditional enterprise telecom bills by up to 75%. It provides efficient security and network data management while saving money.
Hardware vs. Software SBCs
SBCs come in two different forms, hardware and software. Hardware SBCs are similar to any other kind of on-premises equipment. They sit in server rooms hooked up to other physical servers and analog gateways. Alternatively, a cloud-based software SBC will keep your network safe with no on-premises equipment.
As for which one is best, it depends entirely on the user. Most organizations may prefer the software SBC. It's easily integrated into their cloud-based solutions. However, some may prefer the hardware option instead if they still rely on analog devices or legacy systems. These are all integrated with the cloud solution via the SBC.
Maximum Security with Microsoft Teams
Security is extremely vital to Microsoft. It has a plethora of security certifications including HIPAA, HITECH, ITAR FedRAMP, FISMA, EU Model Clauses / Privacy Shield, ISO, SSAE, and SOC 1-3. It fends off 5 billion cyber threats each month with the help of a $1 billion investment in cybersecurity.
Microsoft supports a wide range of hardware and software SBCs. Software SBCs are an integral part of Microsoft Phone System which keep phone calls protected for Office 365 users. Hardware SBCs are used in Direct Routing. The right SBCs allow any PBX or analog gateway to be integrated into Teams.
If you’re already a Teams user or are planning an upgrade soon, chances are you have an integrator at your side helping you implement your solution. Your integrator will be well informed to help you deploy the right Session Border Controller for your system.
Continuant is a trusted integrator. We've been helping organizations deploy and manage communication systems for more than 25 years. We'll find the right SBCs to keep your network secure.
Ready to start your journey to Teams? Schedule an assessment with our experts to make your network more secure.
* Editor's Note: This article was originally published in March 2019 and has been revamped and updated for accuracy and comprehensiveness.

